On March 21, 2025, Oracle Cloud faced intense scrutiny after cybersecurity researchers uncovered evidence of a massive data breach affecting over 6 million users and 140,000 customer domains. Despite Oracle’s initial denial, the breach—attributed to a hacker using the alias “rose87168”—was confirmed by independent firms, including Hudson Rock and CloudSEK. Exposed data includes sensitive credentials such as usernames, emails, LDAP passwords, OAuth2 keys, and encrypted passwords.
Sources:
- https://www.linkedin.com/feed/update/urn:li:activity:7310017463516127232/
- https://www.cloudsek.com/blog/part-2-validating-the-breach-oracle-cloud-denied-cloudseks-follow-up-analysis
Who was the hacker?
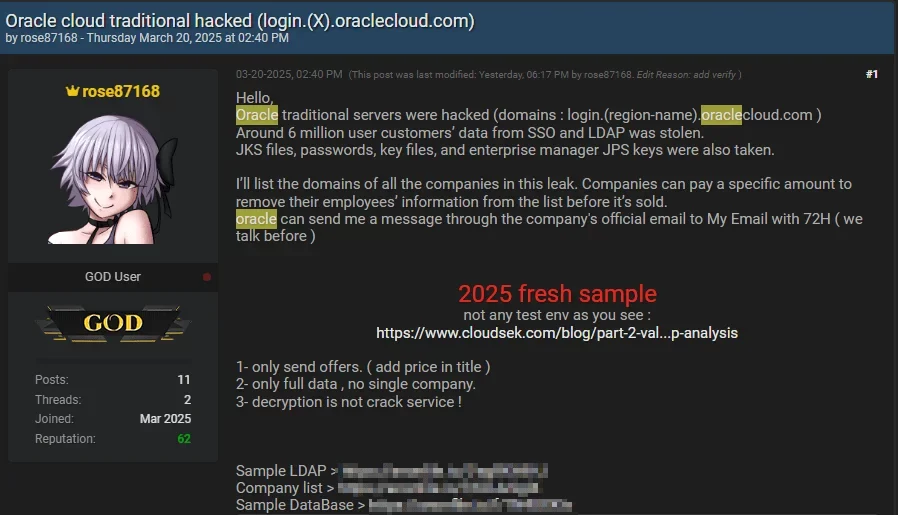
A hacker using the alias “rose87168” claims to have breached Oracle Cloud, compromising approximately 6 million records. Active since at least January 2025, the hacker is reportedly selling the stolen data on dark web forums such as BreachForums and has launched extortion campaigns against affected organizations.

What Information Did the Hacker “rose87168” Allegedly Extract from Oracle Cloud?
The compromised data reportedly includes:
-
Java KeyStore (JKS) files,
-
Encrypted credentials used for Single Sign-On (SSO),
-
Encrypted Lightweight Directory Access Protocol (LDAP) passwords and related key files,
-
Enterprise Manager Java Policy Store (JPS) keys.
These assets are foundational components of Oracle Cloud’s authentication and identity management infrastructure. If genuine, the exposure of such elements could severely undermine the platform’s security posture, potentially enabling unauthorized access and privilege escalation.
How Did the Breach Occur?
The hacker alleges that the breach was achieved by exploiting a weakness in Oracle Cloud’s authentication infrastructure—specifically targeting the login endpoint at login.[region-name].oraclecloud.com. While the exact method remains unconfirmed, cybersecurity researchers, including those at CloudSEK, suggest that CVE-2021-35587—a previously disclosed vulnerability in Oracle Access Manager, part of Oracle Fusion Middleware—could be involved. However, “rose87168” has implied the use of an unpatched or previously unknown vulnerability, raising concerns of a zero-day exploit.
Did Oracle Confirm the Hack?
No. Oracle denied the breach (read more).
What Evidence Has “rose87168” Presented to Substantiate the Breach Claim?
To support their claims, “rose87168” has released sample data allegedly obtained from the breach. This includes text files containing database records and LDAP-related information. Additionally, the hacker uploaded a file referencing their email address to the login.us2.oraclecloud.com endpoint—an action that has been archived on the Internet Archive. While this suggests a potential level of access to Oracle Cloud systems, the authenticity of the evidence has not yet been independently verified.
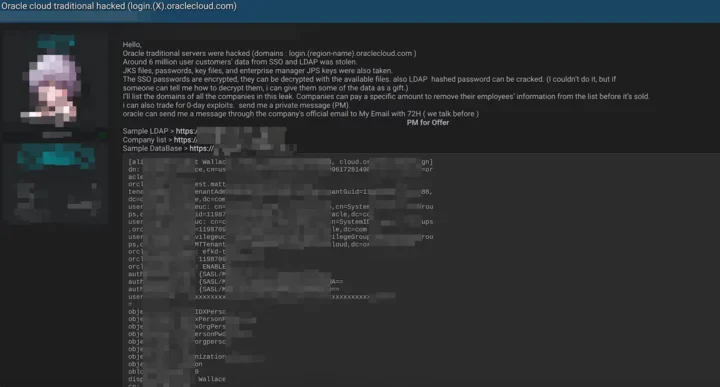
The hacker has shared three sample files as purported proof of the breach: Sample_LDAP.txt, Company.List.txt, and Sample_Database.txt. These files contain excerpts of allegedly stolen data. Sample:
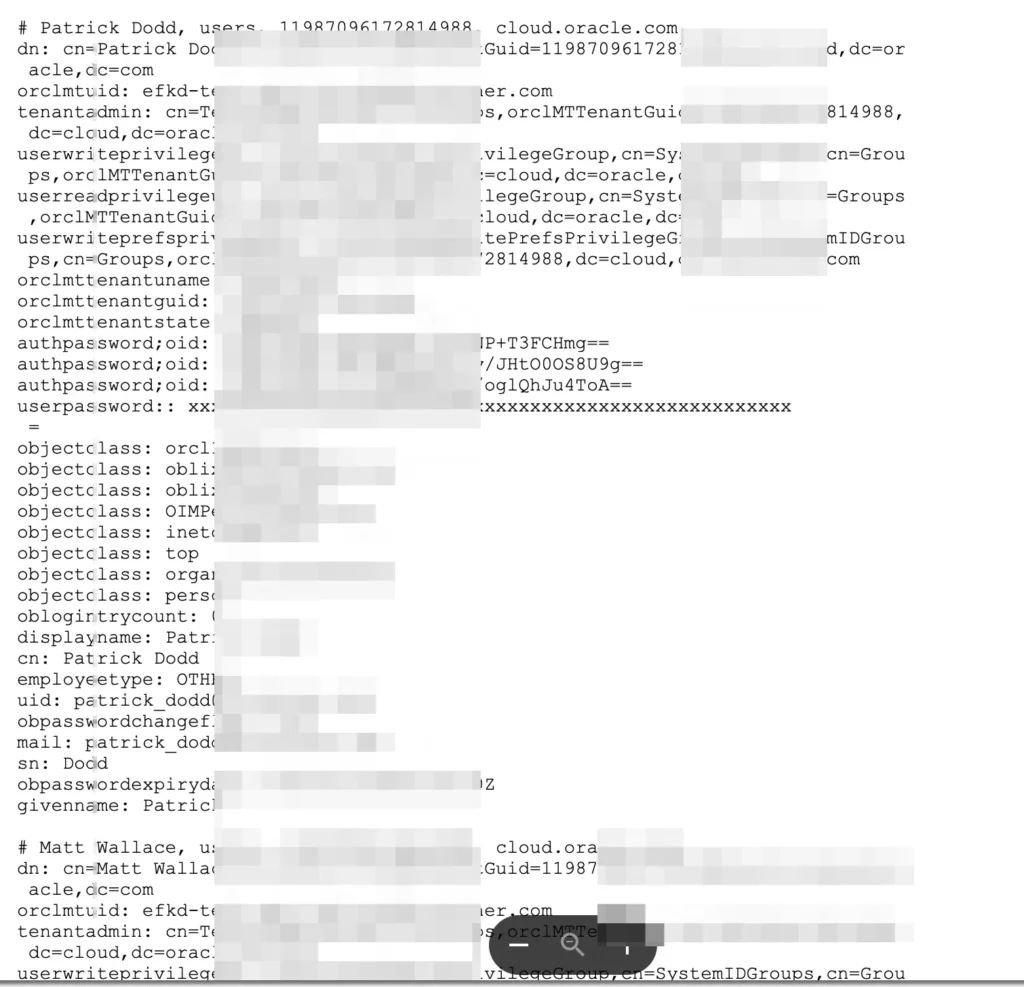
To this day threat actor continued to supply numerous sample screenshots, including the following novel sample data:
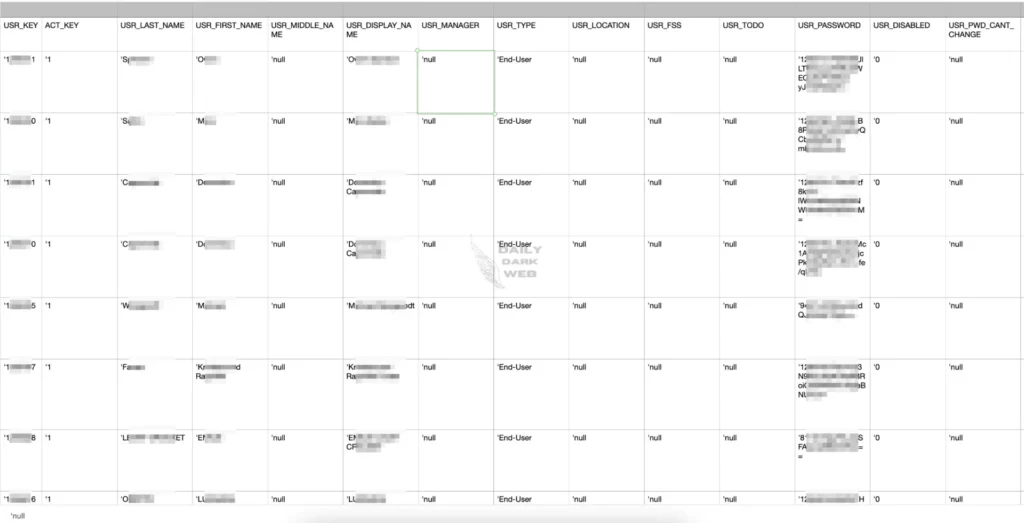
What is “rose87168” doing with the stolen data?
Rose87168 is trying to sell 6 million stolen records on a website called BreachForums. They didn’t say the exact price but are also willing to trade it for dangerous software bugs (called zero-day exploits). They told the companies in the list that they can pay money to remove their data. The hacker is also asking others to help decode stolen passwords.
What Should Organizations Using Oracle Cloud Do in Response?
Security experts urge organizations to take proactive measures, regardless of any official denials, due to the severity of the alleged breach. Recommended actions include:
-
Credential Rotation: Immediately reset all SSO, LDAP, and other related credentials. Ensure Multi-Factor Authentication (MFA) is enforced across all accounts.
-
Incident Investigation: Perform comprehensive forensic analysis to detect any signs of unauthorized access or suspicious activity.
-
Threat Monitoring: Closely monitor dark web forums and breach marketplaces for any signs of leaked organizational data.
-
Engage with Oracle: Coordinate with Oracle’s security team to evaluate potential exposure, apply patches, and stay informed of official updates.
Taking these steps promptly can help mitigate risks and limit potential damage.
How can I keep my Oracle Cloud safe from attacks like this?
-
Update systems: Make sure Oracle Fusion Middleware is updated after October 2021 to fix a security problem.
-
Use MFA: Turn on two-step login for all accounts.
-
Control access: Only allow logins from safe, trusted places (using IP rules).
-
Change keys often: Regularly change special files and passwords used to log in.
-
Watch logs: Set up alerts to warn you if something strange happens in your Oracle Cloud.
Conclusion
While Oracle has yet to issue an updated statement, the confirmed breach demands urgent action from users. Proactive measures—password resets, MFA, and system upgrades—are critical to minimizing fallout.